Why Blockchain Data Protection is Key to Safeguarding Your Ideas in 2025
Your intellectual property deserves bulletproof protection. Let's explore how blockchain transforms ordinary data into an impenetrable digital fortress.
The Numbers Don't Lie: We're in a Digital War Zone
Every 39 seconds, hackers strike somewhere in the digital world. But what if I told you there's a technology that could make your data virtually unbreachable?
The Blockchain Security Boom is Real
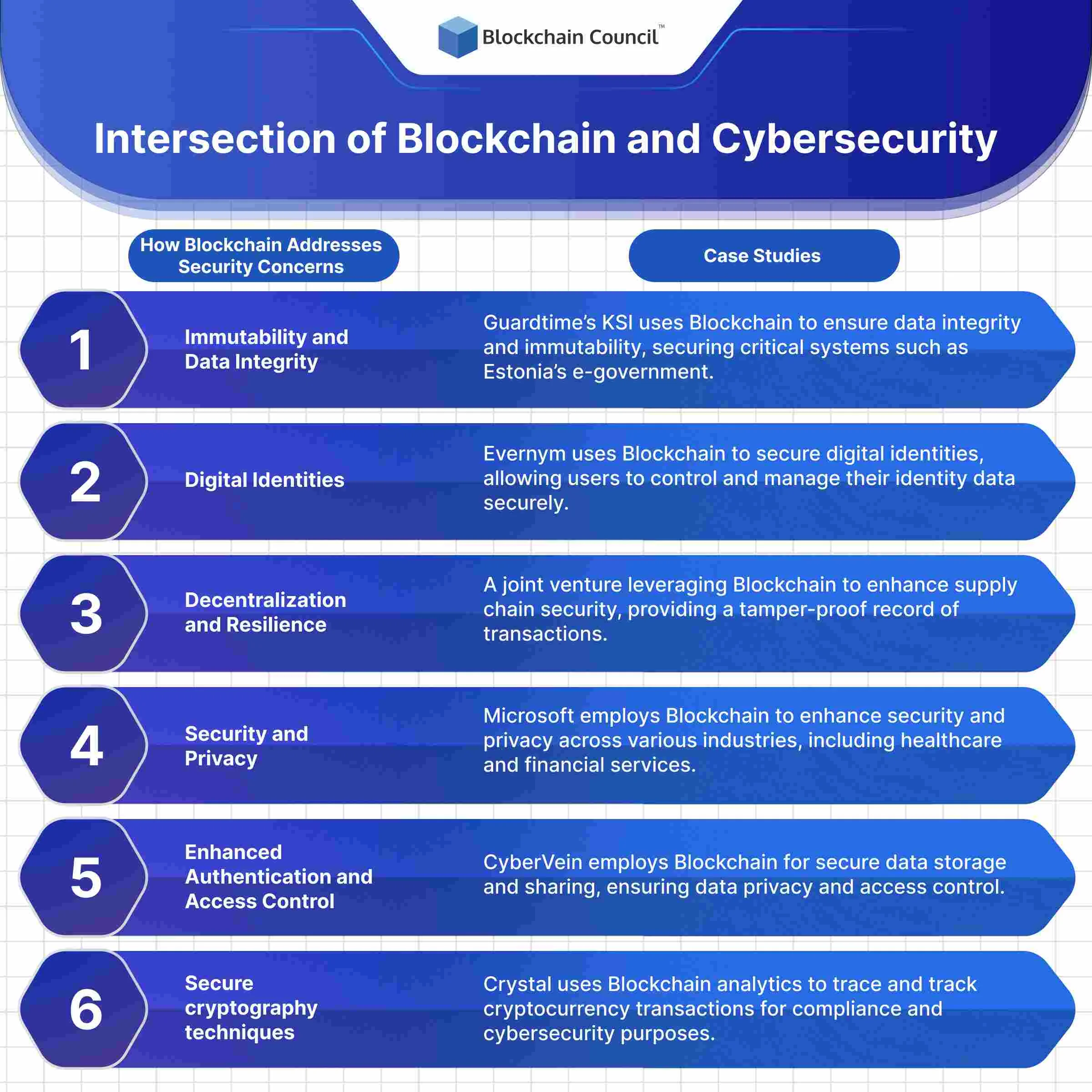
Where Security Meets Innovation
The future is already here
Here's Why Traditional Security Just Isn't Cutting It Anymore
Think about it: when hackers breach a traditional database, they hit the jackpot. But blockchain? It's like trying to rob a bank that exists in a thousand different places at once.
The Game-Changing Difference
Permanent Records
Picture this: every piece of data you store becomes a permanent, unchangeable part of history. No more worrying about someone sneaking in and altering your files.
No Single Target
Instead of keeping all your eggs in one basket, blockchain spreads them across thousands of baskets. Good luck to any hacker trying to steal them all!
Military-Grade Encryption
We're talking about the same level of protection that governments use for their most classified information. Your data becomes virtually uncrackable.
Old School vs. Blockchain Security
Real Talk from Industry Experts
These aren't theoretical concepts - real professionals are using this technology right now
What's Coming in 2025: The Expert View
IBM's technology leaders share insider perspectives on cybersecurity evolution
The Blockchain Security Revolution
See how companies are actually implementing these solutions
The Hottest Blockchain Security Trends Everyone's Talking About
From my conversations with industry insiders, these are the developments that have everyone excited (and some people worried).
Smart AI Guards
Imagine having a security guard that never sleeps, never gets distracted, and learns from every attack attempt. That's AI-powered blockchain security for you.
Quantum-Proof Protection
They say quantum computers will break all encryption. Well, blockchain developers are already two steps ahead with quantum-resistant algorithms.
Invisible Verification
Zero-knowledge proofs let you prove something is true without revealing what it actually is. It's like showing someone you know a secret without telling them the secret.
Corporate Takeover
Fortune 500 companies aren't just dipping their toes anymore - they're diving headfirst into private blockchain networks for mission-critical data.
Legal Framework Formation
Governments are finally catching up with technology. New regulations are creating clear rules for blockchain data handling and privacy protection.
You Own Your Identity
Forget about letting big tech companies control your personal information. Decentralized identity puts you back in the driver's seat of your own data.
Let's Get Real About Today's Security Threats
I've been tracking cybersecurity incidents for years, and the patterns are clear. Here's what keeps security professionals awake at night - and how blockchain addresses each concern.
The Threat Landscape Reality
Massive Data Breaches
$4.45M average costYou know those headlines about millions of user records being stolen? That's what happens when all your eggs are in one digital basket.
Blockchain Solution: No central treasure chest to raid - data is spread everywhere
Identity Theft Epidemic
$56B yearly damageYour social security number, credit card details, and personal info are sitting ducks in centralized databases that hackers love to target.
Blockchain Solution: You control your own identity - no middleman required
Supply Chain Deception
$52B global impactFrom fake luxury goods to contaminated food, supply chains are plagued by fraud because nobody can track what's really happening.
Blockchain Solution: Every product has an unalterable digital passport
Your Step-by-Step Game Plan for 2025
Enough theory - let's talk about actually doing this. I've helped dozens of organizations make this transition, and here's the playbook that works.
The Four-Phase Approach That Actually Works
Foundation Phase (Months 1-2)
Before you build the fortress, you need to know what you're protecting. This phase is all about understanding your current vulnerabilities.
- • Identify your most valuable data assets
- • Map current security gaps and weaknesses
- • Get everyone on board with the vision
Testing Phase (Months 3-4)
Start small and prove it works. Pick one specific use case and build a working prototype that demonstrates real value.
- • Choose a pilot project with clear success metrics
- • Build and test your first blockchain implementation
- • Measure results and gather user feedback
Expansion Phase (Months 5-8)
Once you've proven the concept works, it's time to roll it out across your organization systematically.
- • Connect blockchain with existing systems
- • Train your team on new security protocols
- • Scale up infrastructure and processes
Mastery Phase (Ongoing)
Security isn't a destination - it's a journey. Keep improving, updating, and staying ahead of new threats.
- • Continuous monitoring and threat assessment
- • Regular security updates and improvements
- • Stay compliant with evolving regulations
Your Success Checklist
Pro Tip from the Trenches
Don't try to boil the ocean on day one. I've seen companies succeed by starting with hybrid blockchain solutions that give them control while they learn the ropes. Once you're comfortable, you can always go fully decentralized.
Real Companies, Real Results, Real Impact
These aren't hypothetical case studies - these are actual organizations that transformed their security posture with blockchain technology.
Healthcare Revolution
Medical records that patients actually control, with instant sharing between doctors while keeping privacy locked down tight.
- • Automatic HIPAA compliance verification
- • Seamless data sharing between hospitals
- • Patients control who sees what
Banking Transformation
Financial institutions are using blockchain to create unbreakable audit trails while cutting down on fraud and regulatory headaches.
- • Instant fraud detection and prevention
- • Automated regulatory compliance reporting
- • Drastically reduced transaction processing costs
Supply Chain Transparency
From factory to your doorstep, every product now has a digital DNA that proves its authenticity and journey.
- • Counterfeit products become impossible
- • Quality issues traced in seconds, not weeks
- • Recall processes work like clockwork
Spotlight: How Walmart Revolutionized Food Safety
Here's a story that perfectly illustrates blockchain's power. Walmart was facing a massive problem: when contaminated food hit shelves, it took weeks to trace the source. People were getting sick, and the company was hemorrhaging money on widespread recalls.
The Pain Point
Traditional paper-based tracking meant food contamination investigations took 2-3 weeks, forcing massive precautionary recalls.
The Blockchain Fix
Every product now has a complete, unchangeable history from farm to shelf, stored across thousands of secure nodes.
The Incredible Result
What used to take weeks now happens in 2.2 seconds. That's not a typo - two point two seconds to trace any product back to its source.

The Ultimate Security Showdown: Blockchain vs. Everything Else
I know you're wondering: "Is blockchain really that much better?" Let me lay out the facts side by side so you can see for yourself.
| What Matters Most | Blockchain Approach | Traditional Methods | Clear Winner |
|---|---|---|---|
| Can Your Data Be Tampered With? | Impossible | Happens Daily | |
| What Happens If Servers Go Down? | Nothing - No Central Server | Complete Shutdown | |
| How Much Can You See? | Complete History | Whatever They Show You | |
| How Fast Can You Get Started? | 6-12 months | 2-4 months | |
| What's the Upfront Investment? | Significant | Moderate | |
| Long-term Value and Savings | Exceptional ROI | Average Returns |
What's Coming Next: The Challenges Nobody Talks About
I believe in being honest about both opportunities and obstacles. Here are the hurdles we're working to overcome, and the innovations that will solve them.
The Real Challenges Ahead
The Quantum Computing Clock is Ticking
Experts predict quantum computers could crack today's encryption by 2030-2035. It sounds scary, but we're not sitting around waiting.
The Solution: Quantum-resistant algorithms are already being deployed
Speed and Scale Growing Pains
Current blockchain networks can feel slow compared to traditional databases, especially when handling millions of transactions.
The Solution: Layer 2 technologies and sharding are solving speed issues
Regulatory Puzzle Pieces
Laws like GDPR's "right to be forgotten" seem to conflict with blockchain's "remember everything forever" nature.
The Solution: Hybrid architectures that balance compliance with immutability
The Innovation Timeline
What's Rolling Out When
Where Smart Money is Going
Dive Deeper: Expert Perspectives and Advanced Concepts
Privacy in the Blockchain Age
Understanding how blockchain protects privacy
Quantum-Safe Future
Preparing for tomorrow's encryption challenges
AI Meets Blockchain
The powerful combination reshaping security
Voices from the Front Lines
These aren't marketing quotes - they're real insights from professionals who are living and breathing blockchain security every day.
In my 20 years of cybersecurity work, I've never seen anything change the game like blockchain has. It's not just better security - it's a completely different way of thinking about trust.
The combination of AI and blockchain isn't just the future - it's happening right now. Organizations that understand this will dominate their industries within three years.
I tell my clients: if you're not planning your blockchain security strategy for 2025, you're already behind. The window for competitive advantage is closing fast.
The Bottom Line: What You Need to Remember
After everything we've covered, these are the essential points that will make or break your security strategy.
Unbreakable Foundation
Blockchain creates data that literally cannot be changed or destroyed once it's recorded.
No Weak Links
Distributed networks mean there's no single point hackers can target to bring everything down.
Explosive Growth
65.5% annual growth shows this isn't a trend - it's the new reality of digital security.
First-Mover Advantage
Early adopters will establish unassailable competitive positions before others catch up.
Your Action Plan Starts Now
This Month (Don't Wait)
- Audit your current security vulnerabilities
- Research blockchain platforms that fit your needs
- Calculate the real cost of your current security risks
- Build a business case for blockchain adoption
Next Quarter (Build Momentum)
- Launch a pilot project with measurable goals
- Partner with experienced blockchain security vendors
- Train your team on blockchain fundamentals
- Create a roadmap for full-scale implementation
Your Ideas Deserve Fortress-Level Protection
The question isn't whether blockchain will revolutionize data security - it's whether you'll be leading the charge or playing catch-up.
